Difference between revisions of "Istio on AWS"
| (20 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
== Preface == | == Preface == | ||
The goals of this document is to describe the process of installing istio.io service mesh into kubernetes cluster. <br> | |||
<br> | |||
A service mesh is a dedicated infrastructure layer that you can add to your applications. It allows you to transparently add capabilities like observability, traffic management, and security, without adding them to your own code. The term “service mesh” describes both the type of software you use to implement this pattern, and the security or network domain that is created when you use that software. <br> | |||
<br> | |||
As the deployment of distributed services, such as in a Kubernetes-based system, grows in size and complexity, it can become harder to understand and manage. Its requirements can include discovery, load balancing, failure recovery, metrics, and monitoring. A service mesh also often addresses more complex operational requirements, like A/B testing, canary deployments, rate limiting, access control, encryption, and end-to-end authentication.<br> | |||
<br> | |||
Service-to-service communication is what makes a distributed application possible. Routing this communication, both within and across application clusters, becomes increasingly complex as the number of services grow. Istio helps reduce this complexity while easing the strain on development teams | |||
== Pre-Requisite == | == Pre-Requisite == | ||
To follows this particular case of installation, it is assumed that one has already successfully installed managed kubernetes service in AWS Platform, should one needs detailed instruction to perform the task, please refer to [[Getting Started on Amazon EKS]] page. This should enable one to have deployed manage kubernetes services that manageable from local machine. | |||
== What is istio == | == What is istio == | ||
Istio is an open source service mesh that layers transparently onto existing distributed applications. Istio’s powerful features provide a uniform and more efficient way to secure, connect, and monitor services. Istio is the path to load balancing, service-to-service authentication, and monitoring – with few or no service code changes. Its powerful control plane brings vital features, including:<br> | |||
* Secure service-to-service communication in a cluster with TLS encryption, strong identity-based authentication and authorization Automatic load balancing for HTTP, gRPC, WebSocket, and TCP traffic | |||
* Fine-grained control of traffic behavior with rich routing rules, retries, failovers, and fault injection | |||
* A pluggable policy layer and configuration API supporting access controls, rate limits and quotas | |||
* Automatic metrics, logs, and traces for all traffic within a cluster, including cluster ingress and egress | |||
Istio is designed for extensibility and can handle a diverse range of deployment needs. Istio’s control plane runs on Kubernetes, and you can add applications deployed in that cluster to your mesh, extend the mesh to other clusters, or even connect VMs or other endpoints running outside of Kubernetes.<br> | |||
<br> | |||
A large ecosystem of contributors, partners, integrations, and distributors extend and leverage Istio for a wide variety of scenarios. You can install Istio yourself, or a number of vendors have products that integrate Istio and manage it for you. | |||
== Installing Istio == | == Installing Istio == | ||
In order to install istio.io, first we are | In order to install istio.io, first we are going to download the source into local machine by using below command, at the time this document is written, current version of istio.io is 1.11.2 | ||
curl -L https://istio.io/downloadIstio | sh - | curl -L https://istio.io/downloadIstio | sh - | ||
move to istio folder installation | move to istio folder installation | ||
| Line 41: | Line 59: | ||
Output: | Output: | ||
<title>Simple Bookstore App</title> | <title>Simple Bookstore App</title> | ||
== Exposing Application to outside traffic == | == Exposing Application to outside traffic == | ||
At this point, the application is already running but we cannot access it from the outside. To make it accessible, you need to create an Istio Ingress Gateway, which maps a path to a route at the edge of your mesh. To execute this, there are two step that we need to execute.<br> | At this point, the application is already running but we cannot access it from the outside. To make it accessible, you need to create an Istio Ingress Gateway, which maps a path to a route at the edge of your mesh. To execute this, there are two step that we need to execute.<br> | ||
| Line 56: | Line 75: | ||
Execute the following command to determine if your Kubernetes cluster is running in an environment that supports external load balancers: | Execute the following command to determine if your Kubernetes cluster is running in an environment that supports external load balancers: | ||
kubectl get svc istio-ingressgateway -n istio-system | kubectl get svc istio-ingressgateway -n istio-system | ||
Expected output | Expected output, tabled out from shell output | ||
{| class="wikitable" | |||
istio-ingressgateway | |+ Expected output | ||
|- | |||
| NAME || istio-ingressgateway | |||
|- | |||
| TYPE || LoadBalancer | |||
|- | |||
| CLUSTER-IP || 10.100.32.131 | |||
|- | |||
| EXTERNAL-IP || a63eca23a2998474c9feda458e127103-292095897.us-west-2.elb.amazonaws.com | |||
|- | |||
| PORT(S) || 15021:31607/TCP,80:30526/TCP,443:30361/TCP,31400:30605/TCP,15443:32431/TCP | |||
|} | |||
If the EXTERNAL-IP value is set, your environment has an external load balancer that you can use for the ingress gateway. If the EXTERNAL-IP value is <none> (or perpetually <pending>), your environment does not provide an external load balancer for the ingress gateway. In this case, you can access the gateway using the service’s node port. <br> | |||
There are three environment variable that we need to set inside the cluster's ingress controller to enable the external traffic.<br> | |||
In AWS environments, the load balancer may be exposed using a host name, instead of an IP address. In this case, the ingress gateway’s EXTERNAL-IP value will not be an IP address, but rather a host name, Please use below command to set the environment variables | |||
export INGRESS_HOST=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].hostname}') | |||
export INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="http2")].port}') | |||
export SECURE_INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="https")].port}') | |||
export GATEWAY_URL=$INGRESS_HOST:$INGRESS_PORT | |||
Finally, ensure host and port is setup correctly | |||
echo "$GATEWAY_URL" | |||
== Verify External Access== | |||
Confirm that the Bookinfo application is accessible from outside by viewing the Bookinfo product page using a browser. | |||
Run the following command to retrieve the external address of the Bookinfo application. | |||
echo "http://$GATEWAY_URL/productpage" | |||
Paste the output from the previous command into your web browser and confirm that the Bookinfo product page is displayed. | |||
<gallery> | |||
book.png|Expected output | |||
</gallery> | |||
== Dashboards on istio == | |||
stio integrates with several different telemetry applications. These can help you gain an understanding of the structure of your service mesh, display the topology of the mesh, and analyze the health of your mesh. Use the following instructions to deploy the Kiali dashboard, along with Prometheus, Grafana, and Jaeger. | |||
1. Install Kiali and other addons | |||
kubectl apply -f samples/addons | |||
kubectl rollout status deployment/kiali -n istio-system | |||
Expected output : | |||
<SyntaxHighlight lang=shell> | |||
serviceaccount/grafana created | |||
configmap/grafana created | |||
... | |||
service/prometheus created | |||
deployment.apps/prometheus created | |||
</SyntaxHighlight> | |||
2. Access the kiali dashboard | |||
istioctl dashboard kiali | |||
This command will start default web browser on your machine to access the kiali dashboard through tunneling traffic.<br> | |||
Notes on Graph menu item, on left menu navigation will only displayed trace data after the request has reached minimum sampling rate. Default sampling rate is 1%, please execute below command to access the product-page service. <br> | |||
for i in {1..100}; do curl "http://$GATEWAY_URL/productpage"; done | |||
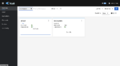
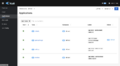
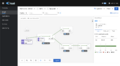
The Kiali dashboard shows an overview of your mesh with the relationships between the services in the Bookinfo sample application. It also provides filters to visualize the traffic flow. Below are the screen capture for kiali dashboard on Bookstore application sample. | |||
<gallery> | |||
Kali-overview.png|Kiali Overview Page | |||
Kiali-app.png|Kiali Application Page | |||
Kiali-graph.png|Kiali Graph Page | |||
</gallery> | |||
== Cleanup == | |||
When you’re finished experimenting with the Bookinfo sample, uninstall and clean it up using the following instructions: <br> | |||
Delete the routing rules and terminate the application pods | |||
samples/bookinfo/platform/kube/cleanup.sh | |||
Confirm shutdown | |||
kubectl get virtualservices #-- there should be no virtual services | |||
kubectl get destinationrules #-- there should be no destination rules | |||
kubectl get gateway #-- there should be no gateway | |||
kubectl get pods #-- the Bookinfo pods should be deleted | |||
Latest revision as of 08:34, 5 September 2021
Preface
The goals of this document is to describe the process of installing istio.io service mesh into kubernetes cluster.
A service mesh is a dedicated infrastructure layer that you can add to your applications. It allows you to transparently add capabilities like observability, traffic management, and security, without adding them to your own code. The term “service mesh” describes both the type of software you use to implement this pattern, and the security or network domain that is created when you use that software.
As the deployment of distributed services, such as in a Kubernetes-based system, grows in size and complexity, it can become harder to understand and manage. Its requirements can include discovery, load balancing, failure recovery, metrics, and monitoring. A service mesh also often addresses more complex operational requirements, like A/B testing, canary deployments, rate limiting, access control, encryption, and end-to-end authentication.
Service-to-service communication is what makes a distributed application possible. Routing this communication, both within and across application clusters, becomes increasingly complex as the number of services grow. Istio helps reduce this complexity while easing the strain on development teams
Pre-Requisite
To follows this particular case of installation, it is assumed that one has already successfully installed managed kubernetes service in AWS Platform, should one needs detailed instruction to perform the task, please refer to Getting Started on Amazon EKS page. This should enable one to have deployed manage kubernetes services that manageable from local machine.
What is istio
Istio is an open source service mesh that layers transparently onto existing distributed applications. Istio’s powerful features provide a uniform and more efficient way to secure, connect, and monitor services. Istio is the path to load balancing, service-to-service authentication, and monitoring – with few or no service code changes. Its powerful control plane brings vital features, including:
- Secure service-to-service communication in a cluster with TLS encryption, strong identity-based authentication and authorization Automatic load balancing for HTTP, gRPC, WebSocket, and TCP traffic
- Fine-grained control of traffic behavior with rich routing rules, retries, failovers, and fault injection
- A pluggable policy layer and configuration API supporting access controls, rate limits and quotas
- Automatic metrics, logs, and traces for all traffic within a cluster, including cluster ingress and egress
Istio is designed for extensibility and can handle a diverse range of deployment needs. Istio’s control plane runs on Kubernetes, and you can add applications deployed in that cluster to your mesh, extend the mesh to other clusters, or even connect VMs or other endpoints running outside of Kubernetes.
A large ecosystem of contributors, partners, integrations, and distributors extend and leverage Istio for a wide variety of scenarios. You can install Istio yourself, or a number of vendors have products that integrate Istio and manage it for you.
Installing Istio
In order to install istio.io, first we are going to download the source into local machine by using below command, at the time this document is written, current version of istio.io is 1.11.2
curl -L https://istio.io/downloadIstio | sh -
move to istio folder installation
cd istio-1.11.2
Add the istioctl client to your path (Linux or macOS):
export PATH=$PWD/bin:$PATH
Then, one can start to install istio on the cluster
istioctl install --set profile=demo -y
Please noted, that we are going to install the demo application. Next step is to create the default namespace for sidecar injection.
kubectl label namespace default istio-injection=enabled
Next, deploy the Bookinfo sample application.
kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml
Inspecting the installation result.
kubectl get pod
Output :
NAME READY STATUS RESTARTS AGE
details-v1-79f774bdb9-2vfgq 0/2 PodInitializing 0 9s
productpage-v1-6b746f74dc-lp2dh 0/2 PodInitializing 0 3s
ratings-v1-b6994bb9-6hftr 0/2 PodInitializing 0 7s
reviews-v1-545db77b95-rt69k 0/2 PodInitializing 0 6s
reviews-v2-7bf8c9648f-tvgn6 0/2 PodInitializing 0 5s
reviews-v3-84779c7bbc-trknm 0/2 PodInitializing 0 4s
kubectl get services
Output :
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
details ClusterIP 10.100.109.10 <none> 9080/TCP 21s
kubernetes ClusterIP 10.100.0.1 <none> 443/TCP 68m
productpage ClusterIP 10.100.151.213 <none> 9080/TCP 15s
ratings ClusterIP 10.100.1.63 <none> 9080/TCP 20s
reviews ClusterIP 10.100.119.183 <none> 9080/TCP 18s
Please ensure all the pod status becomes READY <2/2> before proceed to next step. Verify everything is working correctly up to this point. Run this command to see if the app is running inside the cluster and serving HTML pages by checking for the page title in the response:
kubectl exec "$(kubectl get pod -l app=ratings -o jsonpath='{.items[0].metadata.name}')" -c ratings -- curl -sS productpage:9080/productpage | grep -o "<title>.*</title>"
Output:
<title>Simple Bookstore App</title>
Exposing Application to outside traffic
At this point, the application is already running but we cannot access it from the outside. To make it accessible, you need to create an Istio Ingress Gateway, which maps a path to a route at the edge of your mesh. To execute this, there are two step that we need to execute.
1. Associate this application with the Istio gateway:
kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml
Expected Output:
gateway.networking.istio.io/bookinfo-gateway created virtualservice.networking.istio.io/bookinfo created
2. Ensure that there are no issues with the configuration:
istioctl analyze
Expected Output:
✔ No validation issues found when analyzing namespace: default.
3. Determining INGRESS IP and Ports Execute the following command to determine if your Kubernetes cluster is running in an environment that supports external load balancers:
kubectl get svc istio-ingressgateway -n istio-system
Expected output, tabled out from shell output
| NAME | istio-ingressgateway |
| TYPE | LoadBalancer |
| CLUSTER-IP | 10.100.32.131 |
| EXTERNAL-IP | a63eca23a2998474c9feda458e127103-292095897.us-west-2.elb.amazonaws.com |
| PORT(S) | 15021:31607/TCP,80:30526/TCP,443:30361/TCP,31400:30605/TCP,15443:32431/TCP |
If the EXTERNAL-IP value is set, your environment has an external load balancer that you can use for the ingress gateway. If the EXTERNAL-IP value is <none> (or perpetually <pending>), your environment does not provide an external load balancer for the ingress gateway. In this case, you can access the gateway using the service’s node port.
There are three environment variable that we need to set inside the cluster's ingress controller to enable the external traffic.
In AWS environments, the load balancer may be exposed using a host name, instead of an IP address. In this case, the ingress gateway’s EXTERNAL-IP value will not be an IP address, but rather a host name, Please use below command to set the environment variables
export INGRESS_HOST=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')
export INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="http2")].port}')
export SECURE_INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="https")].port}')
export GATEWAY_URL=$INGRESS_HOST:$INGRESS_PORT
Finally, ensure host and port is setup correctly
echo "$GATEWAY_URL"
Verify External Access
Confirm that the Bookinfo application is accessible from outside by viewing the Bookinfo product page using a browser. Run the following command to retrieve the external address of the Bookinfo application.
echo "http://$GATEWAY_URL/productpage"
Paste the output from the previous command into your web browser and confirm that the Bookinfo product page is displayed.
Dashboards on istio
stio integrates with several different telemetry applications. These can help you gain an understanding of the structure of your service mesh, display the topology of the mesh, and analyze the health of your mesh. Use the following instructions to deploy the Kiali dashboard, along with Prometheus, Grafana, and Jaeger. 1. Install Kiali and other addons
kubectl apply -f samples/addons kubectl rollout status deployment/kiali -n istio-system
Expected output :
serviceaccount/grafana created
configmap/grafana created
...
service/prometheus created
deployment.apps/prometheus created
2. Access the kiali dashboard
istioctl dashboard kiali
This command will start default web browser on your machine to access the kiali dashboard through tunneling traffic.
Notes on Graph menu item, on left menu navigation will only displayed trace data after the request has reached minimum sampling rate. Default sampling rate is 1%, please execute below command to access the product-page service.
for i in {1..100}; do curl "http://$GATEWAY_URL/productpage"; done
The Kiali dashboard shows an overview of your mesh with the relationships between the services in the Bookinfo sample application. It also provides filters to visualize the traffic flow. Below are the screen capture for kiali dashboard on Bookstore application sample.
Cleanup
When you’re finished experimenting with the Bookinfo sample, uninstall and clean it up using the following instructions:
Delete the routing rules and terminate the application pods
samples/bookinfo/platform/kube/cleanup.sh
Confirm shutdown
kubectl get virtualservices #-- there should be no virtual services kubectl get destinationrules #-- there should be no destination rules kubectl get gateway #-- there should be no gateway kubectl get pods #-- the Bookinfo pods should be deleted